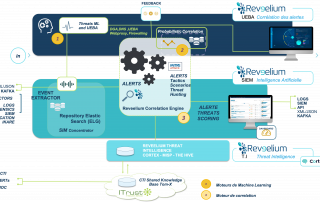
What is a managed EDR or MDR?
Having a managed EDR or MDR is more important than ever today. Here is some useful information to help you in your project to implement a managed EDR. What is an EDR solution? Endpoint Detection Response (EDR) is a set of cybersecurity tools designed to detect and remove any malware or other malicious activity directed against the endpoints connected to your corporate network. Indeed, endpoints and workstations are a prime target for cyberattacks as they are the weakest link in a company's network. As an example, the WannaCry attack exposed the vulnerability of 230,000 endpoints [...]