Above : Feedback from the field
CIOs, CISOs or managers often ask us what the best practices are to apply to protect themselves effectively and quickly.
The first answer I give them is to identify the risks and to set up a simple organization (CISO, DPO, PSSI) adapted to the structure’s functioning.
Within ITrust for 14 years, we have had the time to form an opinion on the best practices, correlating them to those identified by the ANSSI or ENISA or SANS. We have some convictions and we wanted to confirm them with a mini study based on independent recognized standards.
The study is simple. We studied each of the attack techniques used by hackers, malware, insiders, malicious person and we evaluated if the attack method was detected and parried by different technologies: Does an antivirus detect an elevation of privilege, does a firewall detect a C&C used by Emotet, etc. …
For more realism we have studied 2 well done studies by RedCanary and Darkreading that evaluate the most used attack techniques in recent attacks in 2020.
These conclusions are then compared to our field experience. We have identified the attack techniques that ITrust finds in its customers or in its network during the most important attacks or that have the most impact on the company.
We have compared this synthesis with our engineers and we have drawn a conclusion.
Here is the Mitre matrix used with the coverage rate according to the types of technologies.
We did the same thing for Anti virus, Firewall, SIM ….
According to each type of protection technology we have displayed its percentage of coverage of the different MITRE attack techniques. In the following columns we have identified their coverage according to their ability to detect the 10 and 3 most used techniques currently used by hackers and malware. Finally in the last column we identify their coverage rate according to the most dangerous attacks (APT, ransomware, …) evaluated by ITrust’s redteam and Threat Hunting teams.
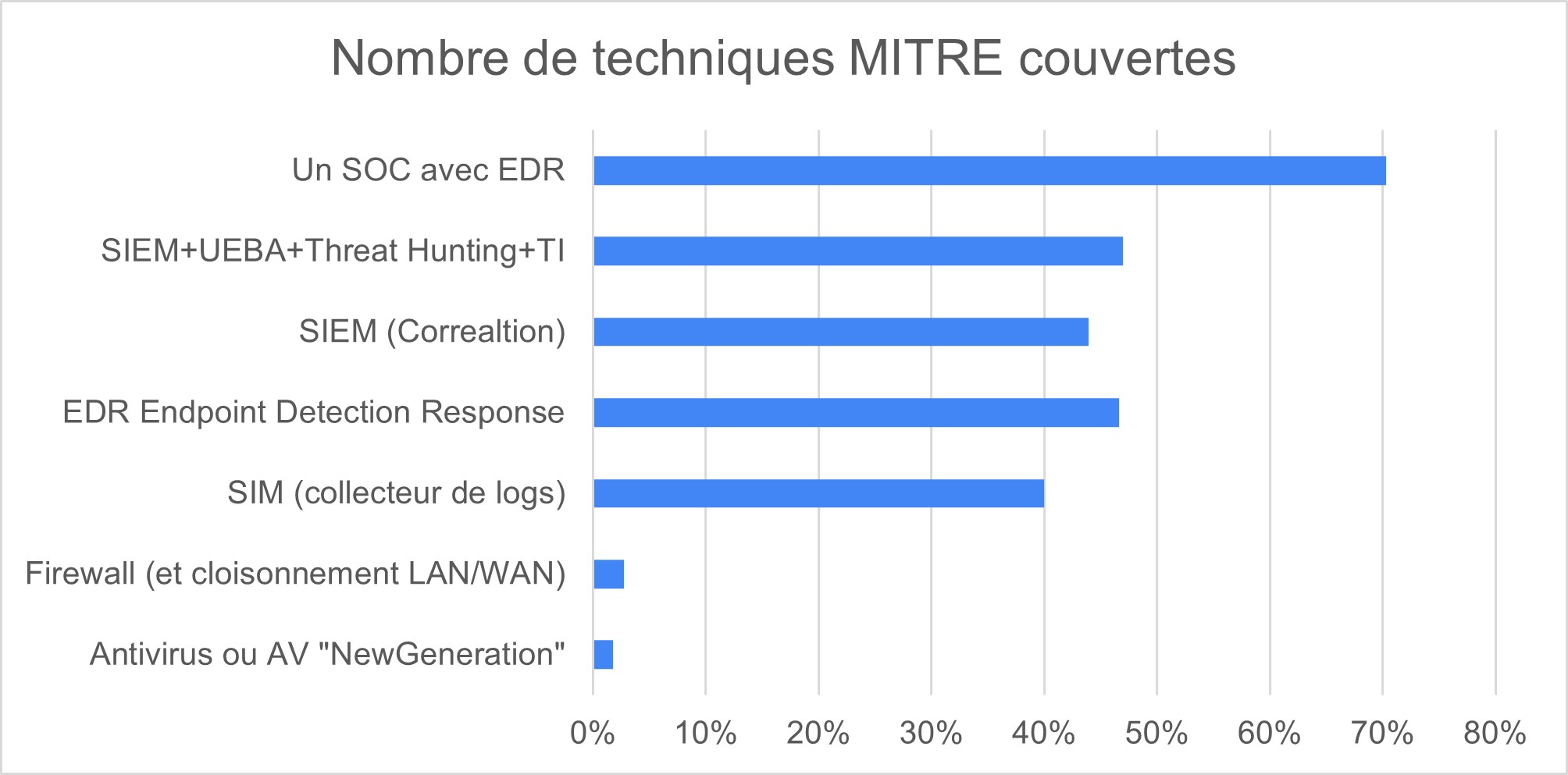
Graph 1 : Number of Mitre techniques covered
Graph 2 : MITRE Techniques covered, among the 3 most dangerous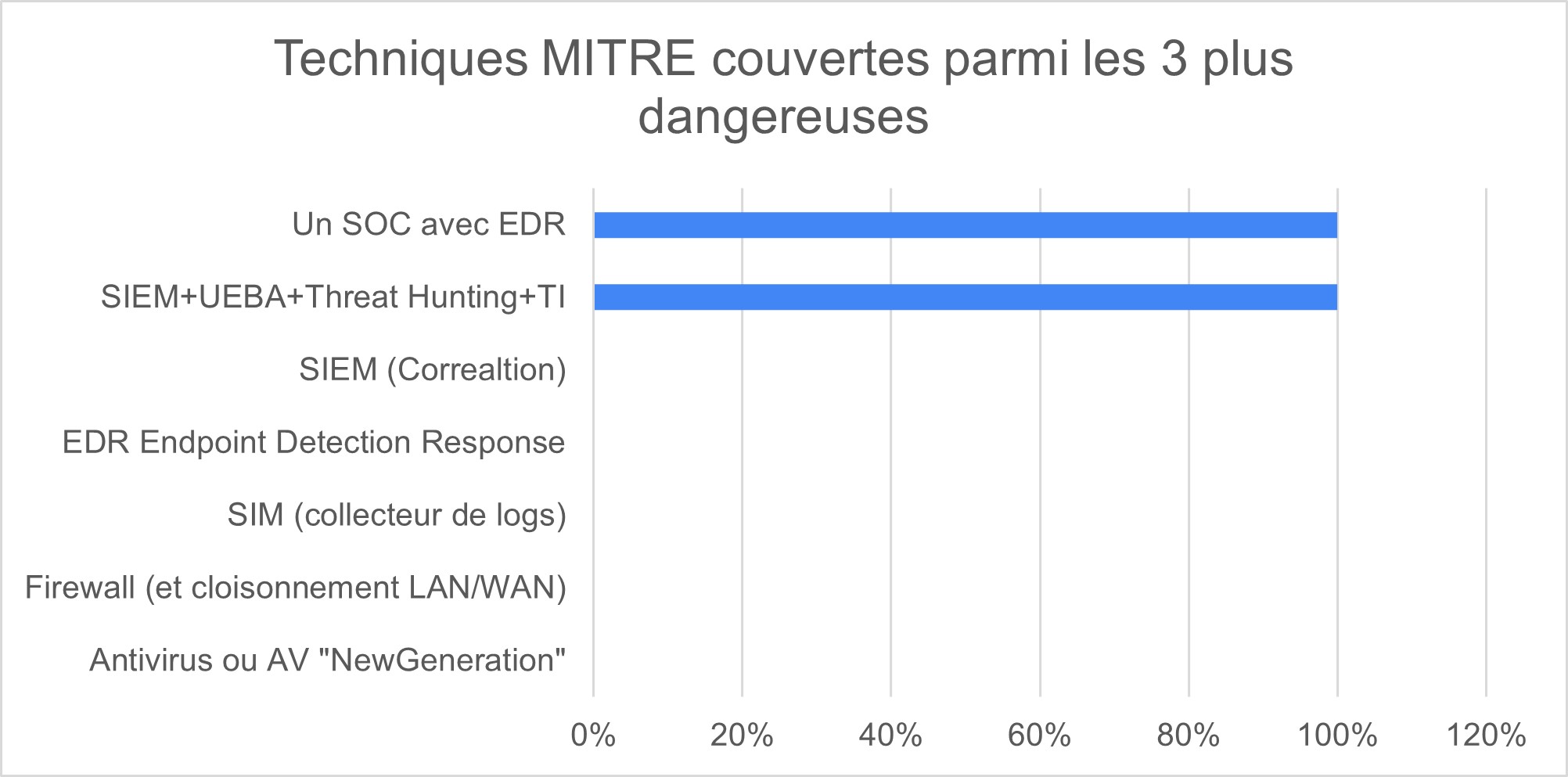
Graph 3 : MITRE Techniques covered, among the 10 most used by pirates / hackers 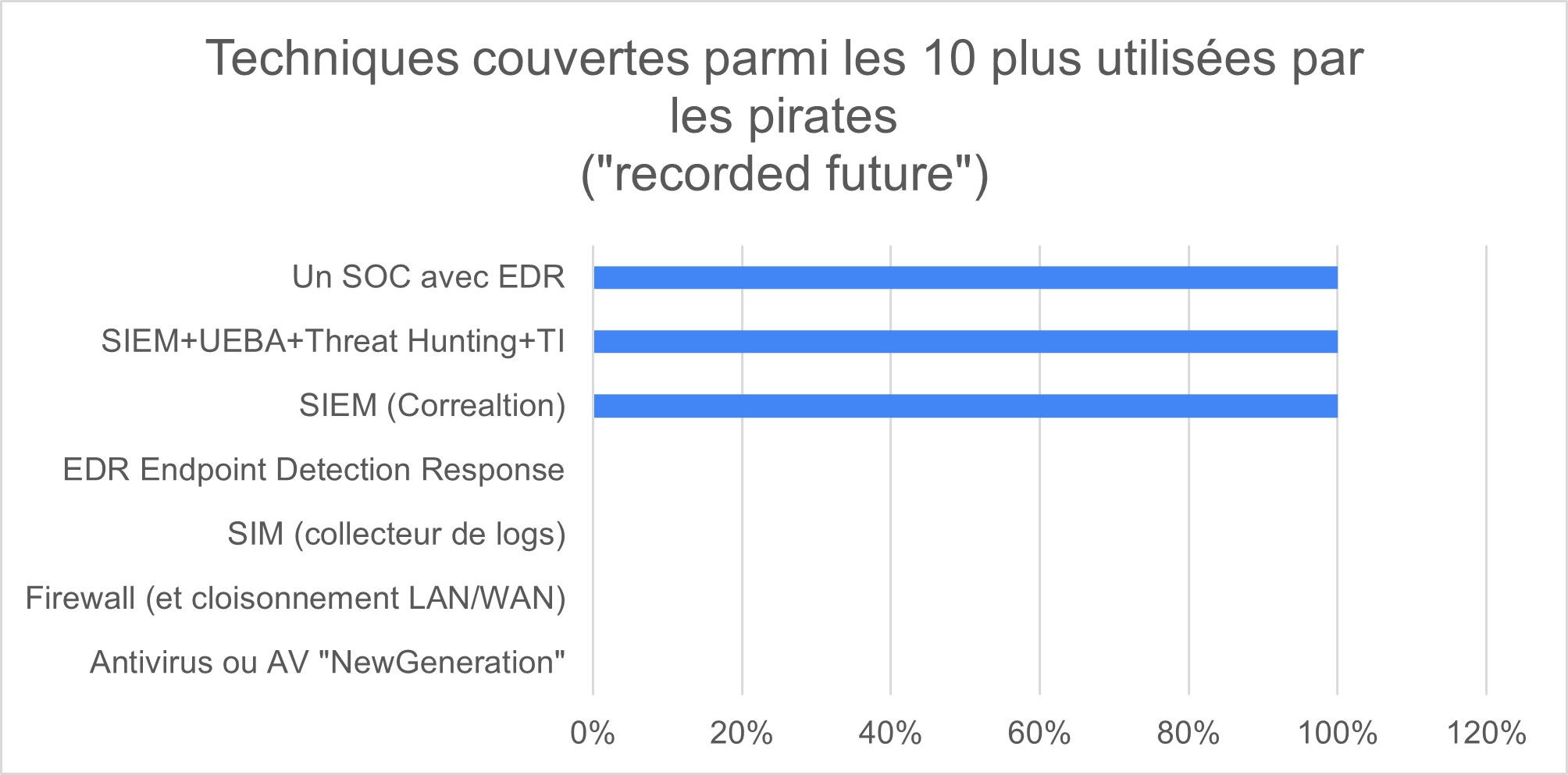
Here is the summary:We notice the non-existent coverage rate of firewalls and anti-virus (although they are essential to cover the most basic risks. We repeat, it is necessary to be equipped with FW and Antivirus!)
An EDR alone has a detection rate that is interesting but will rarely be able to ward off advanced attacks.
The best coverage rate is reached with SOC SIEM UEBA TH. If we add an EDR the detection rate increases by 10% on the RedCanary study.
The feedback and data analysis also indicates that an anti-phishing/anti-spam solution is very complementary. It does not appear in this table.
The “classic” corrective SIEM without UEBA, without artificial intelligence and without threat hunting does not protect against the attacks that have the greatest impact.
Cybersecurity : Protection rates of different technology types, according to recent studies – 2020/ ITrust analysis

Palmares MITRE Matrix
MITRE Matrix Palmares by ITrust
What’s in it for me?
Traditional antivirus and firewall tools are no longer sufficient to protect against 2% of modern attacks
The SOC (Security Operation Center) equipped with a UEBA SIEM has the best detection efficiency to protect against current attacks and more globally has the best coverage rate.
Supplementing a UEBA SOC with an EDR and anti-phishing is relevant. Supplementing a SOC with a vulnerability scanner has become a must.
Based on the experience of ITrust engineers, the recommended solution for any type of company to protect itself is the following:
– a simple risk analysis (simplified Ebios RA)
– an adapted SIP (Security Policy), regularly reviewed and improved in quality cycle
– a CISO (Cyber Security Manager)
– a managed SOC including a UEBA TH SIEM including a continuous vulnerability scanner and an anti-phishing solution,
constitutes a protection package that will allow to protect a company at a very important level (estimated at 100%. This 100% is a dangerous figure because we know that the level is never guaranteed. I would therefore say 99%)
It is advisable to regularly conduct intrusion audits, awareness training, to partition the information system according to the risk analysis performed, to use European cybersecurity tools and to host sensitive data on European cloud providers using European tools and software. Monitoring the darknet or the news of the Cybersec flaws and calling a CERT is interesting and completes the protection in an interesting way.
Be careful not to fall into the classic traps: a SIM is not a SIEM, a new generation anti-virus is not an EDR (it only detects known patterns unlike an EDR), an XDR is not a SOC, …
Beware of cybersecurity insurance, they are not applicable to a large number of hacking cases, not very mature at this time. They will be worth looking into in 2 years.
Beware, 70% of current SOCs do not detect new threats, notably for the reasons mentioned here, but also because of a lack of implementation of a good monitoring, escalation and communication process between teams. Good processes represent 50% of success according to itrust experts.
For the record, a normal cybersecurity budget corresponds to 7% to 13% of the IT budget. (depending on the type of company and the sector). With a lower budget, it is impossible to guarantee anything.
That’s it, it couldn’t be simpler or more effective. Thanks to Itrust engineers and our customers for this feedback.
Some of the information presented in this article is factual as it is supported by independent studies, others are interpretations or opinions of our consultants and experts and can be discussed with pleasure. Let’s note that we encourage all companies to equip themselves with an antivirus and a firewall at least and to conduct a risk analysis to identify the assets and activities to protect. We don’t try to protect everything, we try to make it difficult to access what is valuable.
The goal is for the malicious person to attack someone else who is less protected and for whom he will have less work to do.




