The SOC on demand
Security Operation Center / Security Monitoring Centre
in Saas, Hybrid, Managed or Semi-Managed or OEM
75% of SOCs fail to detect new threats
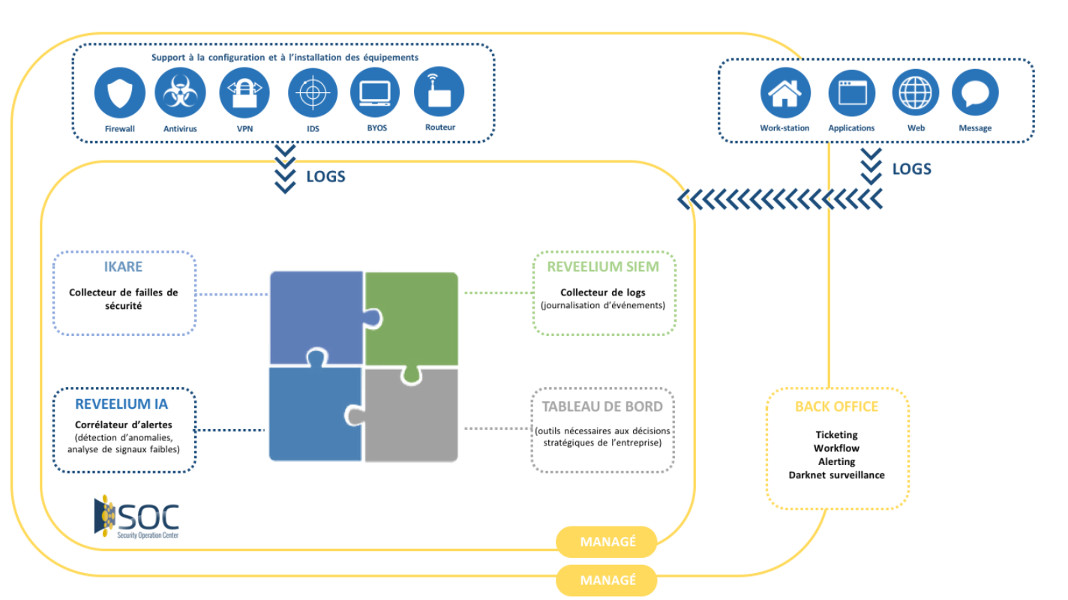
The Control and Supervision Center managed by ITrust, Security Operation Center (SOC), aims to supervise all or part of an organization’s security. Thus, you can concentrate on your core business by entrusting the cybersecurity of your information system to IT security professionals.
Also known as MSSP (Managed Security Services Provider) or MDR (Managed detection and response), we offer to manage the security of your company to protect it and intervene in case of an incident.
This service includes a unique artificial intelligence technology “Elected best cyber security product in 2019 by CIO Applications, in the United States“: Reveelium within the SOC is a SIEM UEBA behavioral analysis technology that allows to detect known and unknown cyber threats: APT (Advanced Persistent Threat), unknown malwares, viruses, leaks, data theft, abnormal behavior within information systems and to trace back the origin of the cyber attack. Combining AI, Threat Hunting, Threat Intelligence, SOAR (“Orchestration, Automation and Response to Computer Security Incidents”), Reveelium allows you to capitalize on events that may threaten the information system, and thus anticipate threats.
Key Strengths
The SOC (Security Operation Center) set up and/or operated by ITrust allows you to optimize your cyber protection while ensuring the availability of your services at the best possible cost, in compliance with specific regulations. The clear and customizable graphical interface allows users to have a precise view of what is happening and to supervise the security of servers, routers, applications, databases, websites…
Because the ability to understand and analyze the events of an information system is essential to ensure its security, we propose and outsource the management of the ISS by our engineers and expert consultants or by our partners (SOC as a franchise).
ITrust’s SOC functions can be installed and/or sold as a software platform and/or operated and/or managed.
The SOC is thus On Premise or Hybrid or Cloud. It can be managed by your teams, ours or our white label partners (OEM or Franchise).
Benefits of the solution
Detect advanced threats
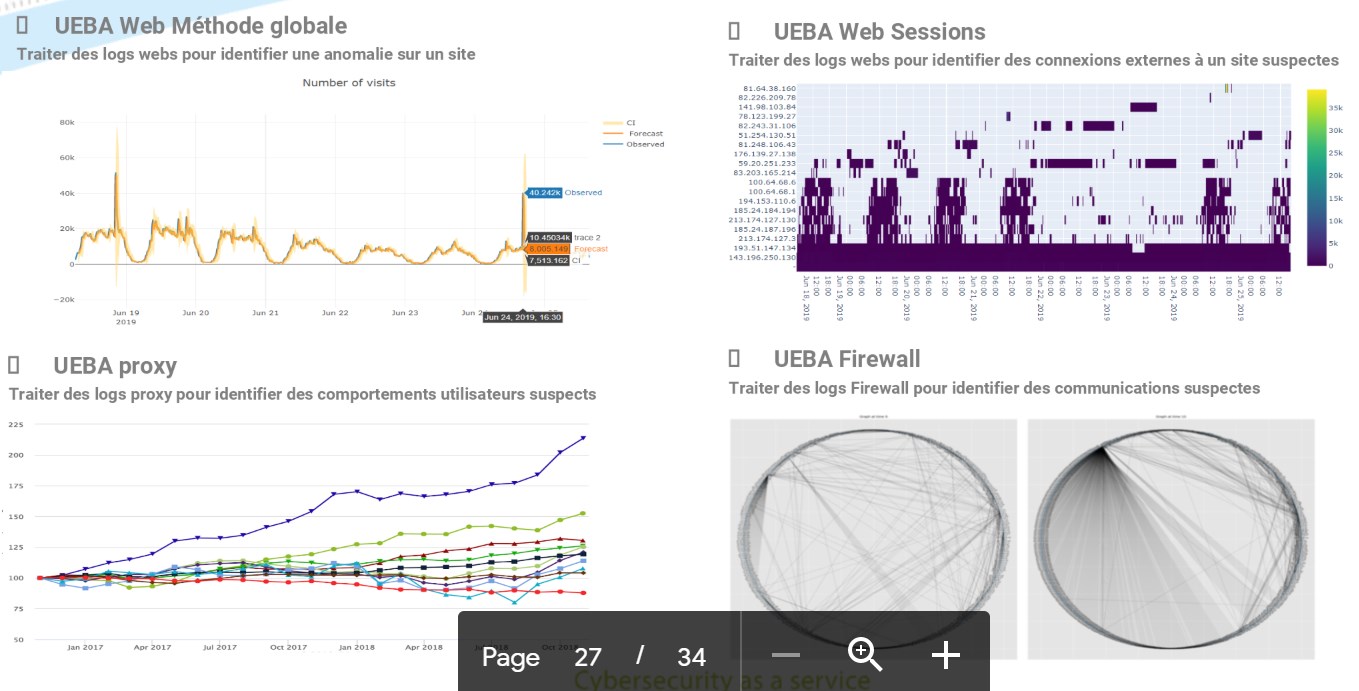
Artificial intelligence and machine learning technologies applied to ITrust’s SIEM UEBA allow a behavioural analysis of the entire information system. This makes it possible to ensure the detection of advanced threats, which only 20% of market players are capable of covering. Although these threats are still not very widespread, they are the most costly and damaging to the information system.
Reduce false positives
The SOC Reveelium allows to reduce false positives in the information system, reduce detection times.
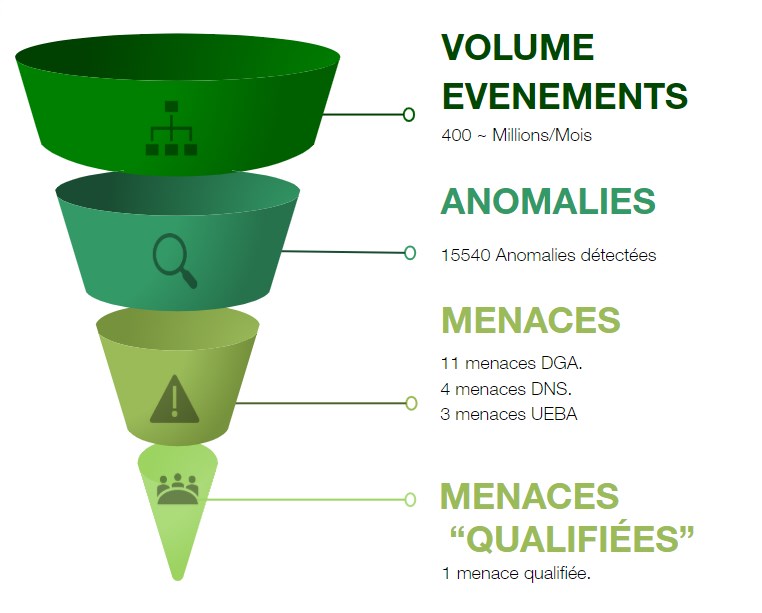
Capable of processing a large amount of logs, the ITrust security center allows the detection of weak signals efficiently from the moment of the attack, which considerably reduces the impact of the attack.
Be alerted in real time
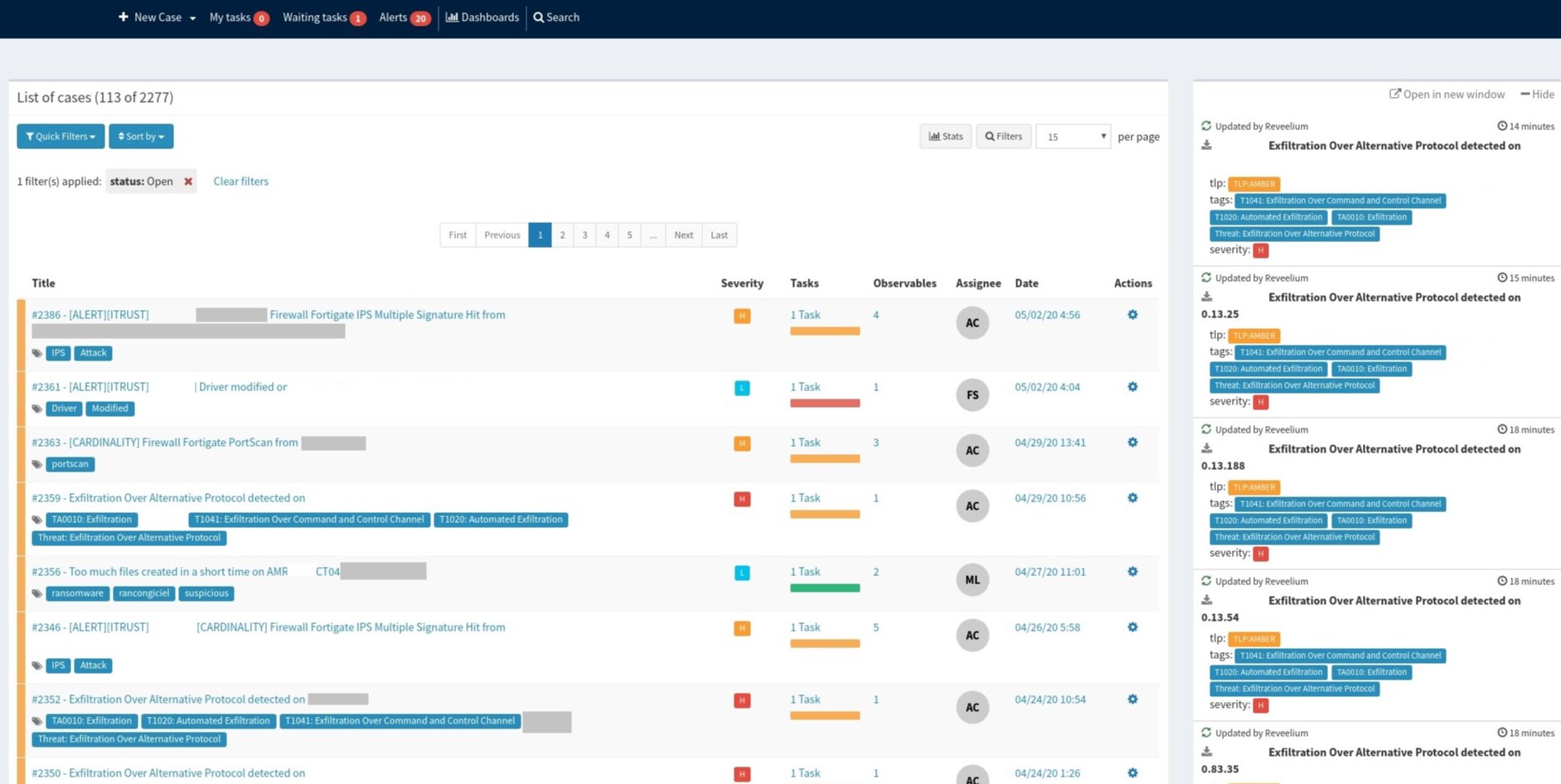
The matrix-based alerting system MITRE allows the identification of “scored” and “prioritized” Threats among millions of events analyzed in real time.
The SOC is associated with IKare, a vulnerability management solution allowing real-time detection of information system security vulnerabilities,
web applications or websites.
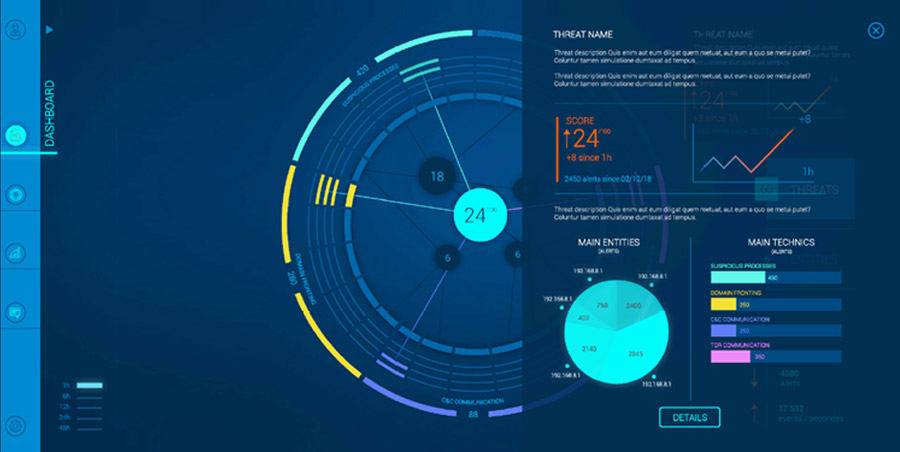
Generate clear reports
The dashboard, automated and customized, provides real-time feedback on field information (SIEM, Reveelium, IKare Monitoring, EDR) and allows you to cross-reference the assets, vulnerabilities and threats your structure faces in order to establish your level of risk day after day.
Compliance dashboards are available for any type of profile: Manager, General Management, Risk Manager, CIO, CISO.
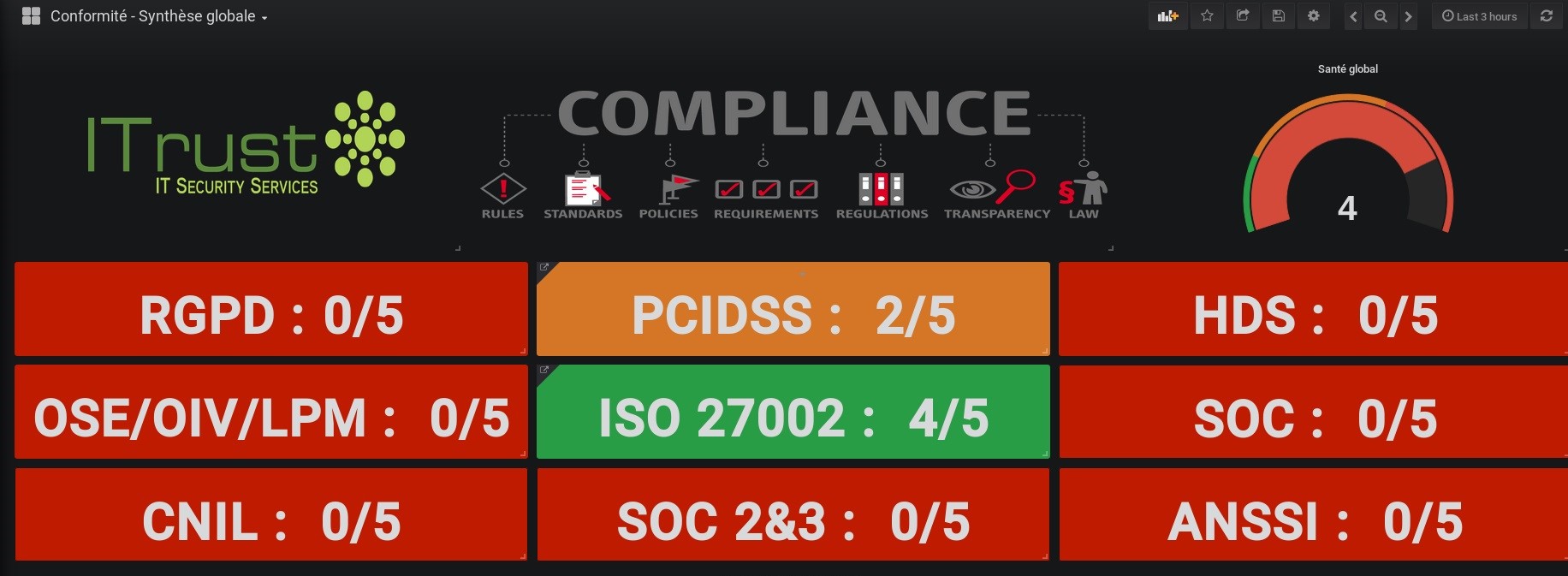
Maintain regulatory compliance
The implementation of a SOC makes it possible to comply with the various regulations, in particular the RGPD, which require, among other things, ensuring
monitoring of vulnerabilities, setting up an incident response strategy or security surveillance.
SOC partner (white label or franchisee)
ITrust proposes to its partners to market a SOC offer in different forms :
The packaged SOC can be proposed to your customers in supervised mode.
or unsupervised, directly usable by your teams.
Nimbly deploy the SOC
The SOC is offered in Infrastructure On Premise mode at the customer’s site, in SaaS outsourced on demand or in Managed (MSSP) mode by ITrust teams.
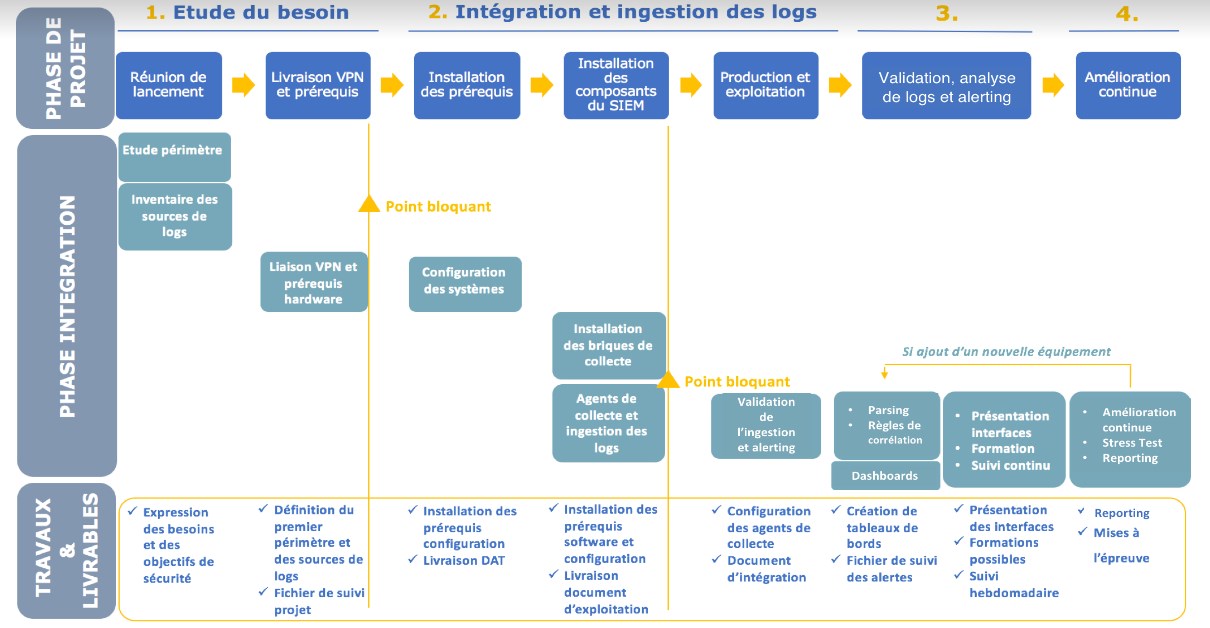
The deployment phases at ITrust are optimized in order to allow our customers to have an operational SOC as soon as possible, i.e. in an average of 5 days.
Optimize cyber ROI
Changing the level of one’s IT security often represents high costs that are difficult to allocate and skills that are difficult to centralize. The implementation of an external or hybrid SOC makes it possible to mutualize the costs of structures, to have experts on demand and thus maximize its return on investment (ROI).
The SOC Sovereign plug and play
“All in One”, the complete SOC of ITrust :
Our clients talk about it…
“We were looking for a service provider
capable of understanding the issues of our
market and to guarantee us an improvement of
the security of our information system. The
solutions proposed by ITRUST, the proximity of
its teams, its expertise in
detection of vulnerabilities and its know-how
in the management of a NCS have known us
convince.”
“We chose ITrust’s software SOC to oversee the department’s cloud to secure the highly sensitive data it contains. We were convinced by the detection capabilities of the artificial intelligence engine and by the expertise of ITrust’s teams”.
“The implementation of the SOC Reveelium allowed us to detect an APT (ransomware) that was spreading in the company. The detection, which would have taken several months under normal circumstances, was immediate and allowed us to avoid the blocking of the information system, saving us a lot of money”.
Learn more about the SOC
Demo SOC

Everything you ever wanted to know about the SOCs
Datasheet UEBA and SOC
Reveelium’s AI modules
Understand how an NCS enables full compliance with the RGPD
How to comply with RGPD with a scanner and a SOC
From the SOC you want some! (blog itrust)
Comparison of SIEM and SOC solutions on the market
They trust the SOC ITrust
Labels & Certifications

















