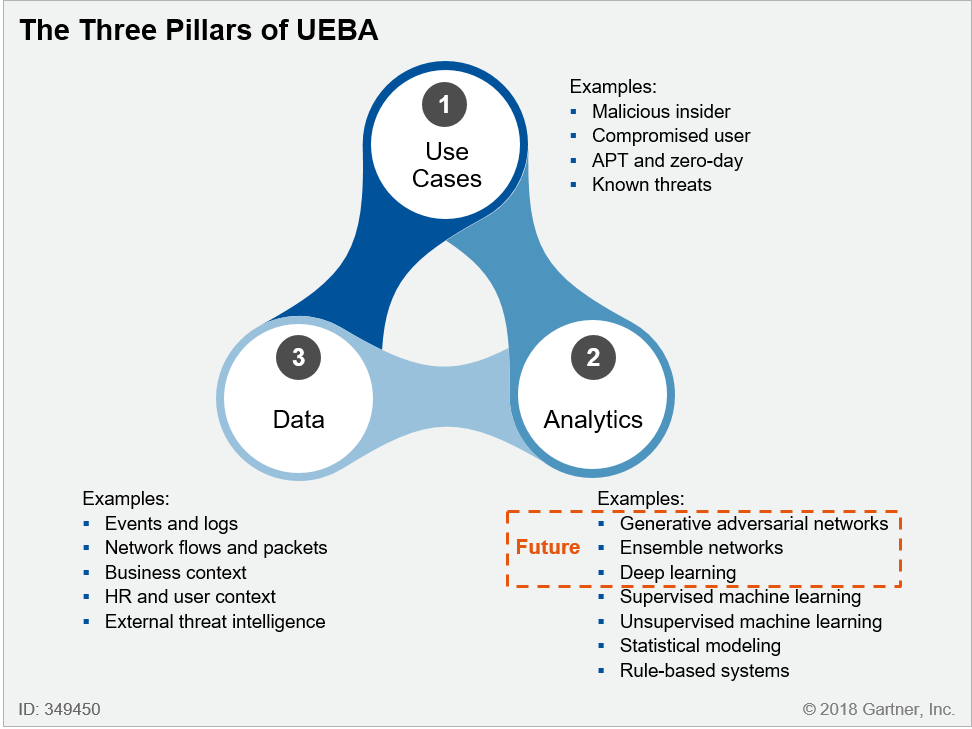
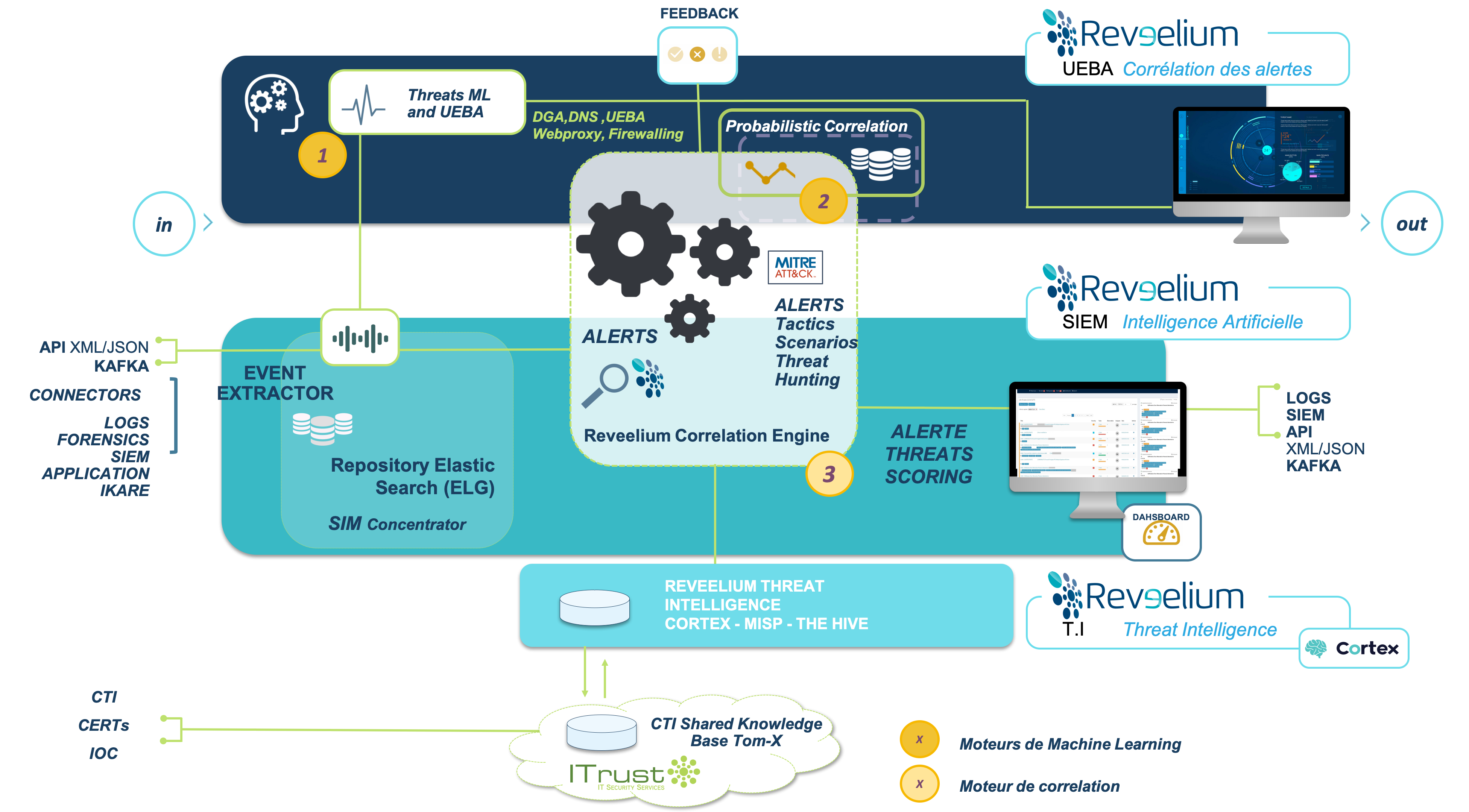
How does Reveelium UEBA / TreatHunting SIEM work?
The principles that govern the operation of SIEM (Security Information Event Management) tools have been well known for years. The arrival of artificial intelligence for cybersecurity tools is less well known. We try to explain it simply here, despite the important technical knowledge usually necessary to fully understand the functioning of very innovative AI technologies.
The logical building blocks :
- A SIM: Security information management: it centralizes and aggregates logs from applications, equipment, security tools (FW, antivirus, proxies, etc…). An advanced SIM can generate some alerts based on (simple) search criteria in the databases. Within Reveelium we use an elastic / Graylog database to centralize the data we receive.
- Example: a dangerous windows event, an antivirus detection event
- A Reveelium SIEM (it also contains the SIM): this tool correlates the events received in order to detect tactics and/or techniques of attacks (cf Mitre), or maliciousness, based on scenarios, threshold criteria or numbers.
- Example: A chain of alerts corresponding to a Mitre maliciousness.
The correlation engine (3) of Reveelium can process various inputs : events, logs, alerts, threats from the AI engine, probabilistic threat results or threat intelligence data. Simple SIEMs available on the market, on the contrary, only perform simple correlation.
The Reveelium SIEM is coupled with our AI / UEBA engine which allows it to :
– detect weak signals that cannot be detected by scenarios or patterns (such as ransomware, APT, etc).
– reduce the number of false positives, to increase the productivity of surveillance teams and reduce the noise generated by these false alerts.
The challenge is to process a very large amount of data and return the best detection, the best scored, prioritized with the least number of false positives.

The UEBA / Threat Hunting Reveelium Engine: provides significant machine learning processing capabilities. It is able to :
- Detect abnormal behavior (1) based on events and logs from the SIM/SIEM.
For example: abnormal user behavior on proxies, abnormal communications on firewalls or DNS, signs of a possible compromise.
In this way, it qualifies attack techniques that cannot be detected by conventional methods of patterns or scenarios. Most of the UEBA SIEMs on the market are very poorly armed and equipped with these techniques. Reveelium is one of the 5 technologies in the world that embeds these detection capabilities.- Example: detection of a DGA during the propagation of Petya in 2016, allowing to avoid the activation of the ransomware attack that affected our client Saint-Gobain (60ME of potential losses)
- Correlate (2) in a probabilistic way (release end of 2020) all alerts, detected techniques, threats thanks to a “unique in the world” behavioral engine
- Example: Enable the detection of a dangerous behavior among a very large number of events or alerts without scenarios or patterns.
- Score and prioritize Threats (all identified malicious techniques and tactics) in order to reduce the processing time by an operator, reduce the reaction time and increase the detection capabilities of the blue team.
- Example: Petya resulted in 3 threats scored at 80/100 instead of 300 alerts that were impossible to process.
Correlation engines (2) and (3) allow us to respond to the following problem identified by Gartner and our customers:

The AI-based behavioral and probabilistic detection engine has been developed by ITrust since 2010. It is recognized as a disruptive technology by the market (see the awards received)
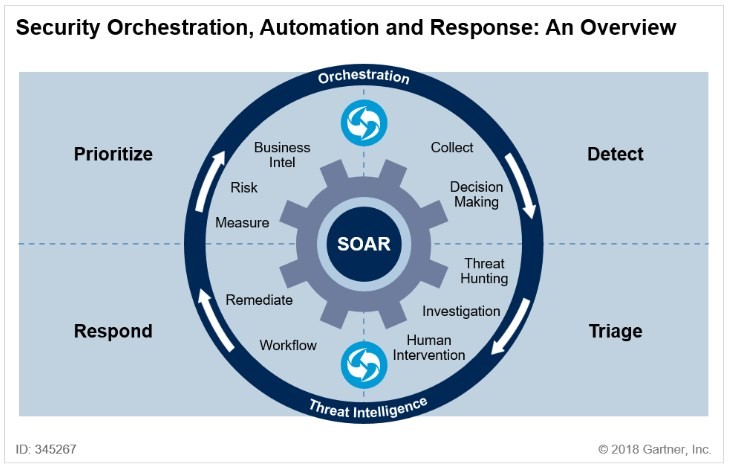
Reveelium SIEM and Reveelium UEBA/Threat Hunting work in coordination and share the same SIEM correlation engine and the probabilistic correlation engine (IA) in order to provide a powerful SOC (Security Operation Center):
- better prioritization of the detection
- fewer false positives
- a threat scoring on the Mitre repository, allowing a gain of time and of detection capacity called SOAR (with the addition of the Acsia EDR module)
- an alerting system (The Hive)
- A workflow and case management system for a better detection
- A possibility of interfacing with a vulnerability scanner (IKare) and an EDR (ACSIA)
- A reporting system to provide dashboards related to a particular activity: Health, PCI/DSS, regulatory compliance, etc…
- KPIs (indicators) adapted to the profile of the people (managers, executives or experts)