Reveelium SIEM
Security Information Event Management
Ever-increasing risks and losses
3 out of 4 companies are subject to computer attacks or hacking (source Verizon).
However, 90% are equipped with essential security equipment that does not detect these malicious attacks. APTs, malicious behaviors, viruses, cryptolockers, override existing security defenses and no current tool can detect these attacks. Yet these attacks leave footprints of their passage.
Finding these malicious traces on a large amount of data and exploiting these signals is impossible with current tools.
Reveelium correlates and aggregates all types of logs from an information system and detects attacks or malicious activity in progress.
Essential tool in the fight against cyber-malware Reveelium SIEM can be used alone or complemented by Ikare, Reveelium UEBA or ITrust’s Acsia EDR, to provide a true next-generation security center (SOC).
8 TIMES OUT OF 10, A HACKED COMPANY DOESN’T KNOW IT!
Our Assets
Understanding and analyzing observable events on an information system is essential to ensure its security.
SIEM has become an essential building block for any company. It is essential to ensure a defense in depth to face new threats. Here are our principles:
A flexible solution, easy to use, which allows us to offer our customers a product SIEM high performance at a lower cost.
Advanced Features
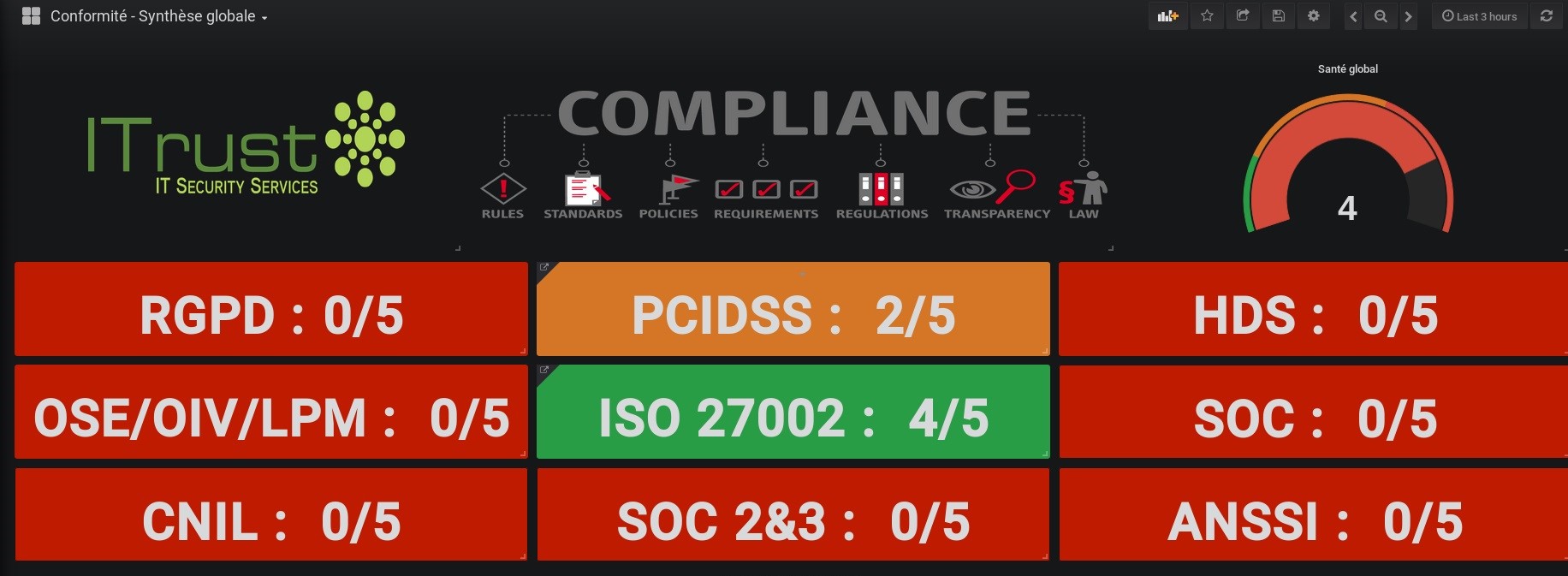
Regulatory compliance
The role of this brick is to collect and archive logs from the datacenter equipment and to restore indicators and dashboards adapted to the company’s security policy.
In the blink of an eye, Revvelium allows you to manage your entire cybersecurity policy for a variety of profiles: Experts, managers, compliance managers, DPOs, CISOs and directors. Reveelium provides a dozen default dashboards and allows you to design your own indicators adapted to your ISSP.
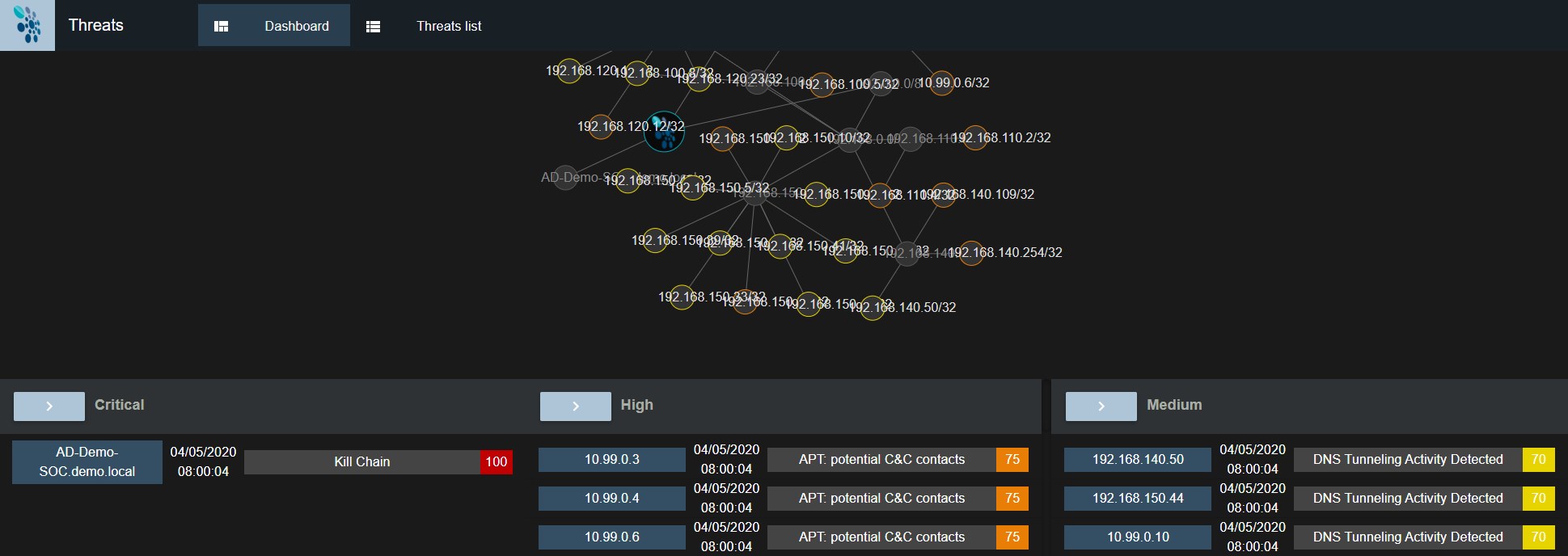
Investigation, Analysis
SIEM allows you to centralize your logs, infrastructure logs, cloud and internal applications. You can organize your logs using tags and use the robust search capabilities of Reveelium and Elastic to discover precise contextual information about your infrastructure. You can also set up alerts to notify you automatically when important events occur in your system.
When it comes to troubleshooting, it’s not always easy to know where to start. Reveelium SIEM automatically visualizes the main trends that appear in your data. Simply click to drill down and up through the data sets, helping you to identify trends and anomalies related to a problem, and find the source of the problem.
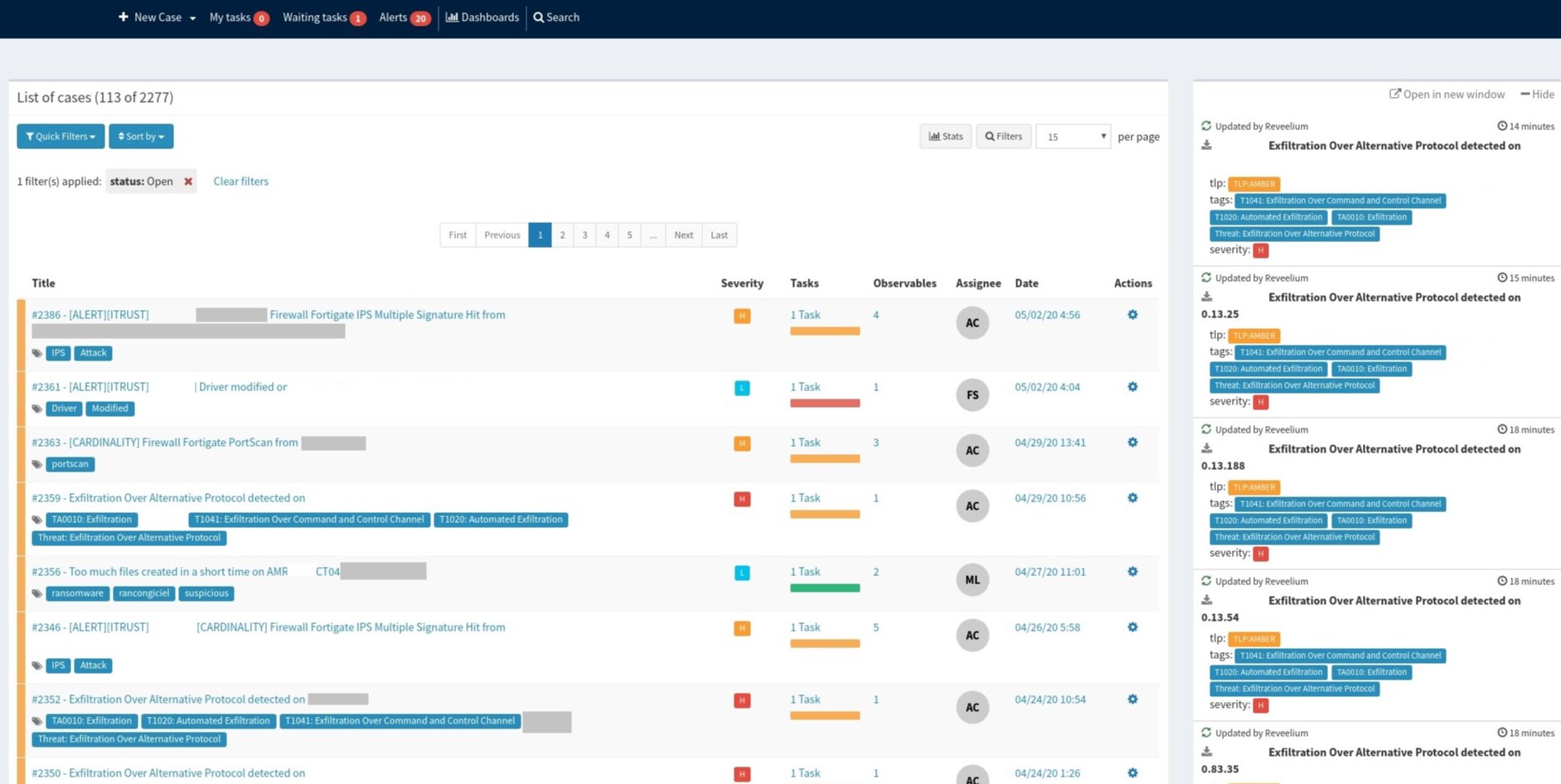
Detection, Correlation, Alerting
You can use the Alerts feature to receive automatic notifications for important events occurring in your environment.
Reveelium allows you to create different types of alerts and “boxes”.
More than 600 Sigma and detection and correlation rules are included by default in Reveelium.
When you create alerts, Reveelium guides you through an alert wizard. At any time, you can switch to another alert or learn more about alerts in the Alert Overview page.
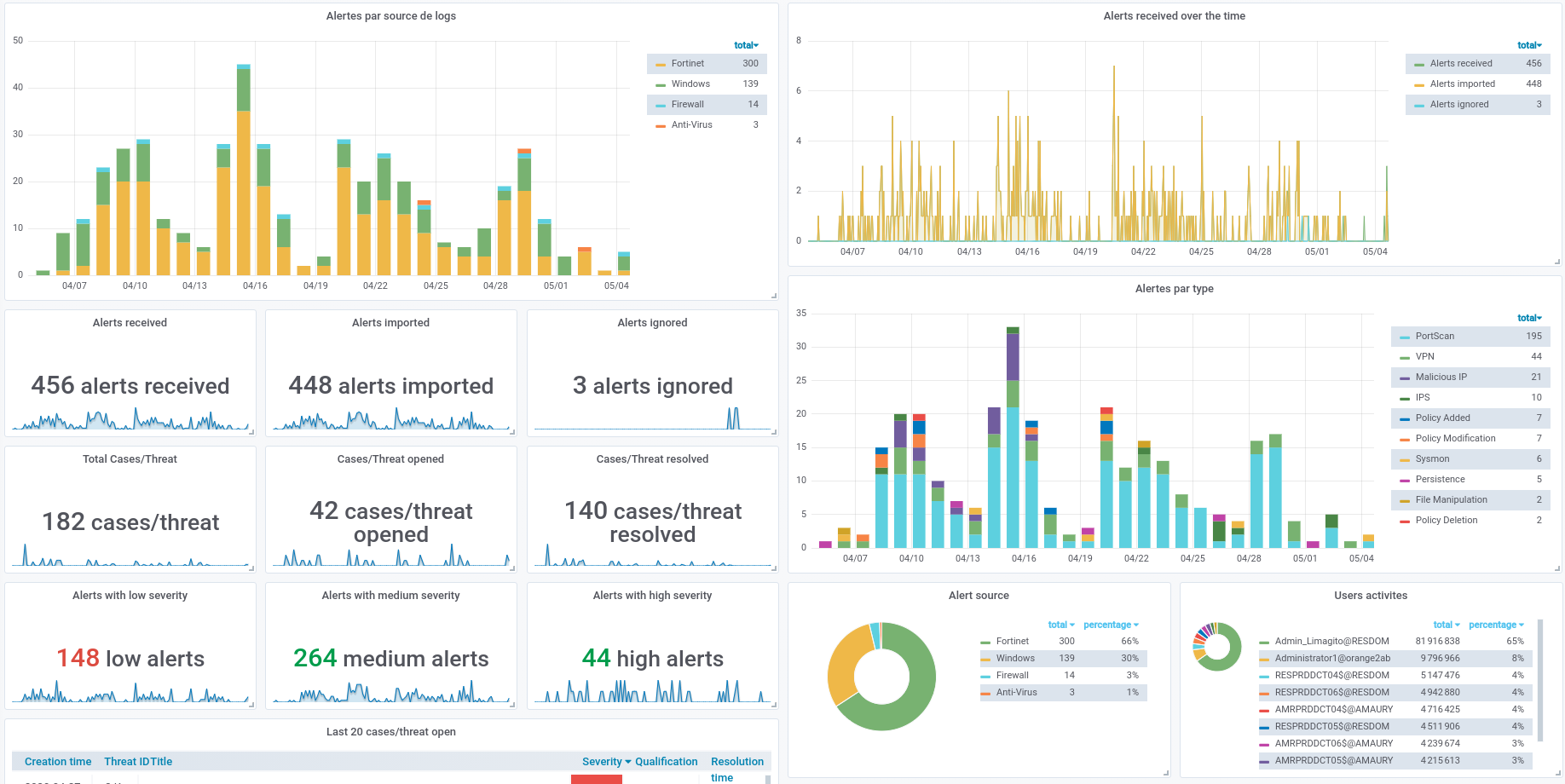
Reporting and indicators
The graphical web frontend allows the analysis and creation of dashboards based on indexed data.
This graphical engine allows to :
Perform searches,
Quickly identify a rare event,
Visualize trends,
Track management and development indicators,
Define compliance indicators,
Create custom dashboards. Dashboards can integrate multiple rankings, graphs, trends… to meet the needs of different users: operators, safety managers, decision-makers…
To go further
They trust Reveelium
Our clients talk about it
“We hadn’t identified any products on the market that could protect us against advanced cyber threats. Until we discovered Reveelium. We have been using it for several years and it allows us to move from a reaction model to a prevention model. We haven’t had a single incident for several years with this technology…”
“Reveelium allows us to monitor in real time our regulatory compliance with SOX and RGPD. My auditors are satisfied with the reports that I extract from the tool. I save time, I gain peace of mind, and in case of an incident I can certify that I am compliant with my obligation of means with respect to NIS directives, the company controls its regulatory risk.”
“Reveelium was able to detect a major intrusion into our system and enabled us to prevent a Cryptolocker attack. Our bank needs to protect its strategic assets and Reveelium is the right tool to do so. It allows us to easily detect malware, reduces our detection time, reduces our analysis time and the size of the teams we need to protect ourselves.”














