Test the robustness of your SOCs
With its expertise in IT security, ITrust is able to test the detection capacity of your Security Operations Centre (SOC).

Context
Faced with the explosion of cybercrime risks, a series of legal provisions oblige companies to secure their information systems and data.
The RGPD, the HDS monitoring and the LPM through directives are becoming the new legislative standards for the protection of :
- Personal data
- Information systems of vital importance (Order of 10 June 2016)
- Protections of medical data
Although different from each other, these regulatory constraints make it mandatory to declare to the CNIL and the ANSSI any loss of data or malicious behavior that the structure may suffer.
You have set up a SOC or are evaluating the possibility of setting up a SOC. You wish to verify :
- The detection capacity of the SOC tools, SIEM, alerting, scanner, probes…
- Decision-making processes and SLAs for your teams or the SOC service provider
- That the SOC is configured according to best security practices (PDIS, legal archiving, base attack detection)
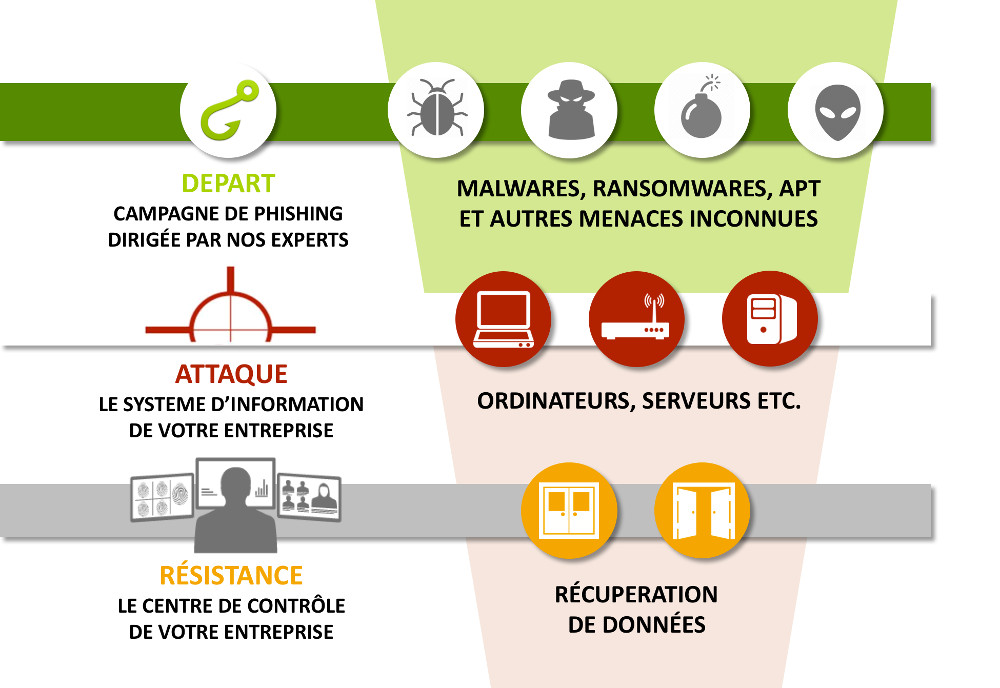
- That the SOC detects new threats such as ransomware, APT, data mining (DLP), spying, phishing, malware, DNS tunneling and many more…
You need certainty and to test the capabilities of your NCS or your supplier’s NCS, or even the NCS you want to implement. We test it for you (in production or in the mock-up phase) with the latest attack techniques.
Course of the Stress Test SOC
Beyond the legislative aspect, ITrust is able to accompany you in the detection tests of your SOC.
A team of slopeters and developers will accompany you throughout this project.
Why trust ITrust ?
- ITrust develops and operates its own SOC. We are experts in SOC and know their detection weaknesses.
- We have been experts in penetration testing for more than 10 years (founder of the Federation of Intrusion Testing Professionals, labeled France Cybersecurity, ARJEL, …).
- Our unique SOC stress test offer covers the entire detection capability. We don’t just perform intrusion tests, we test the ability of SOCs to detect the latest threats.
- We establish an audit label for your SOCs so that you can provide it to your regulatory authorities.
