Make vulnerability management easy with IKare
Master computer vulnerabilities with IKare
IKare is a tool that automates the implementation of security best practices and vulnerability management.
You get a simple network monitoring solution, as well as quick management and easy control of key security factors. You thus increase IT security by 90%. IKare is 10 times more effective than an antivirus or firewall.
99.9% OF ATTACK TECHNIQUES USE 10 CRITICAL SECURITY HOLES.
STRENGTHS
When computer vulnerabilities are identified by a malicious person, they can be exploited, allowing unauthorized access to a computer network or confidential information, stealing trade secrets, using personal data for fraudulent purposes, paralyzing business activity, and many others.
Every day, new vulnerabilities appear due to flaws in systems and applications and poor equipment configurations. It is therefore essential to take action to secure your IS.
Advantages of the solution
Automated & Continuous Vulnerability Audit
IKare provides organizations with a single console to launch and manage recurring vulnerability scans. The network is automatically discovered and vulnerabilities are escalated in near real time and classified in order of criticality according to CVSS standards. IKare allows a very high recurrence of scans, thus guaranteeing the integrity and impermeability of your network from day to day.
Reduced risk of intrusion
A unique scanner developed by ITrust, the fruit of our consultants’ experience in intrusion testing, detects your network assets, associated services, open ports, and traces security breaches related to non-compliance with good security practices. IKare detects default passwords or weak encryption keys and thus guarantees a high level of security by protecting your information system from the most frequent threats.
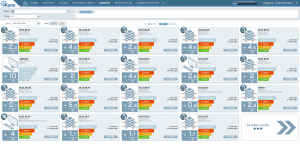
An intuitive administration console
IKare makes it easy for CISOs to manage security and collaborate with technical teams. The dashboards and reports can be adapted to the different levels of the company, from top management to technicians, allowing everyone to access the level of detail that corresponds to their needs.
Simplified management of virtual groups or business units
IKare allows organizations to easily create and organize virtual groups, for example with servers that serve the same function (DMZ, Messaging, Marketing, Accounting etc.) or comply with the same compliance constraints (RGPD, ISO etc.), thus facilitating the management of complex networks. Business Units can be managed individually or consolidated for centralized results management.
Regulatory compliance
The deployment of IKare makes it possible to monitor compliance with various regulations. For example, the RGPD or the HDS require, among other things, monitoring of vulnerabilities. IKare ensures compliance with best security practices on your network through its proactive search for security vulnerabilities. The IKare API allows you to interface the scan results with all types of applications including Risk and Security Governance (RSM) software.
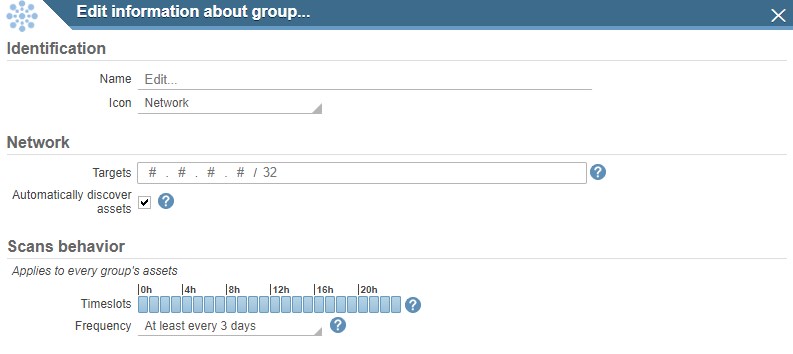
Solution non-intrusive
With its technology and algorithm designed to use only a small amount of bandwidth, our IKare vulnerability scanner has no negative effect on the information system. IKare can be installed in minutes on a physical or virtual server. It allows centralized reporting of several IKare installed in different LANs.
IKare the simplest security solution on the market
The IKare vulnerability management solution analyzes computer networks and detects misconfigured devices, weak passwords or failures and non-updated applications. IKare helps both small and large organizations maintain a secure IT environment. It performs continuous assessments to detect new vulnerabilities in time, and helps accelerate risk mitigation or remediation.
IKare is provided as a virtual machine for internal deployment and/or as a service, to perform on-demand scans from ITrust infrastructures.
The benefits of IKare for you and your customers
Our clients talk about it…
“We have the solution in Cloud mode. Support responds very quickly.
The advantages of deploying IKare: Exporting reports. We use the
product for the CHU and all gfc44 facilities. As soon as we
detect a vulnerability on a facility, we just have to make a
extraction of the report that we send by email to the correspondent
of the site in question so that the improvement can be made. We do not
can’t get any easier than that.”
“The products we had found needed a lot of
modifications and adaptations to our own problems and finally do not
didn’t fit our specifications, it didn’t show up
not in the other solutions we tested. At ITrust, they were able to create
people associated with groups and networks…”
“We replaced our Qualys scanner supplied by the bank’s headquarters with that of ITrust: the solution is very simple to install, in the form of a virtual machine, so it’s almost immediate. Technically, it’s excellent, with flaws that we didn’t detect before! Very fast implementation and the local service is very appreciable.”
They trust IKare
Labels & Certifications




















