IKare
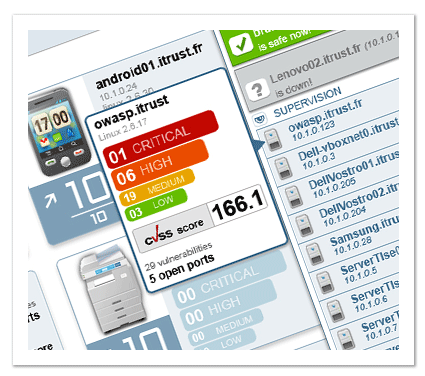
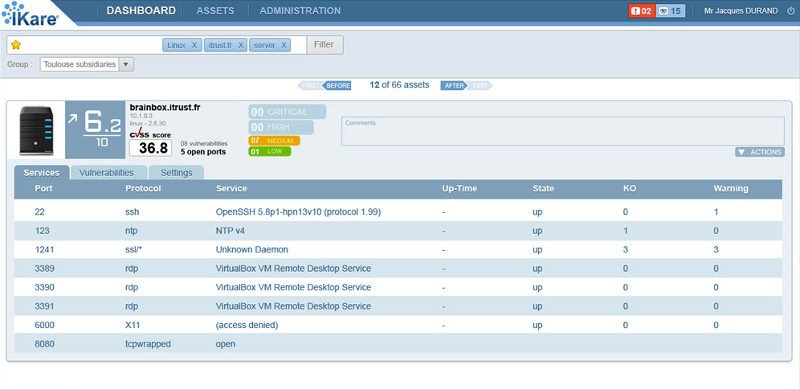
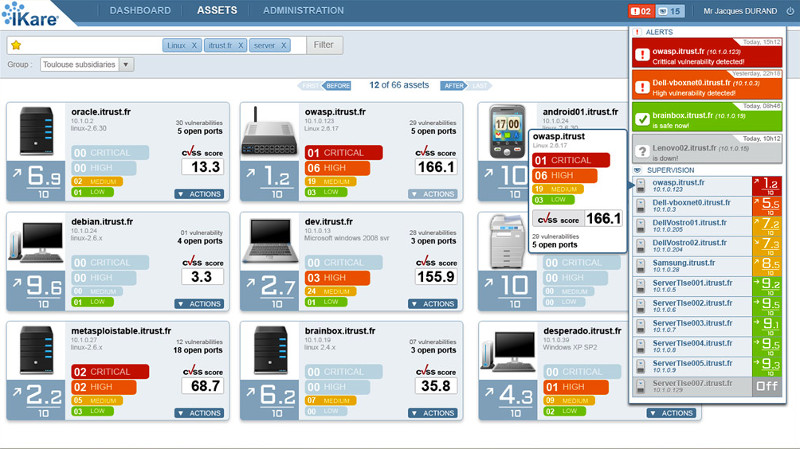
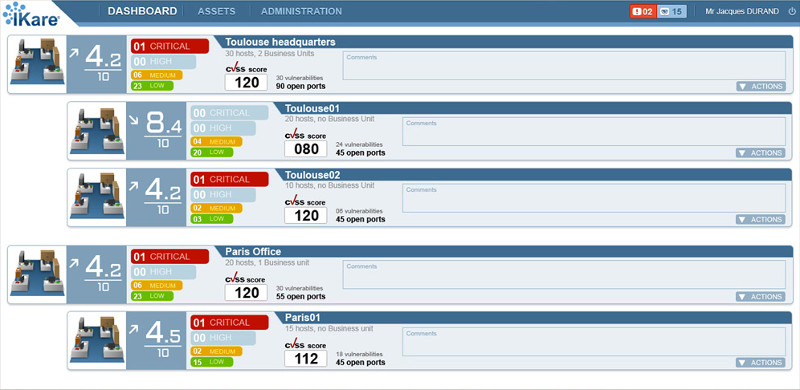
IKare is a tool that automates the implementation of security best practices and vulnerability management.
You get a simple network monitoring solution, as well as easy management and control of key security factors. This increases IT security by 90%. IKare is 10 times more effective than an antivirus or firewall.
When computer vulnerabilities are identified by a malicious person, they can be exploited, allowing unauthorized access to a computer network or confidential information, stealing trade secrets, using personal data for fraudulent purposes, paralyzing business activity and many others…
Benefits of the solution
Models
IKare is provided as a virtual machine for internal deployment and/or as a service to perform on-demand scans from ITrust infrastructures.
IKare is supplied in 3 models:
- IKare on premise – on-site deployment
- IKare cloud – scans from the cloud in SaaS mode
- IKare managed – IKare + an engineer