Your managed EDR in addition to an antivirus
Get real-time threat detection and remediation for your endpoints with our managed EDR solution
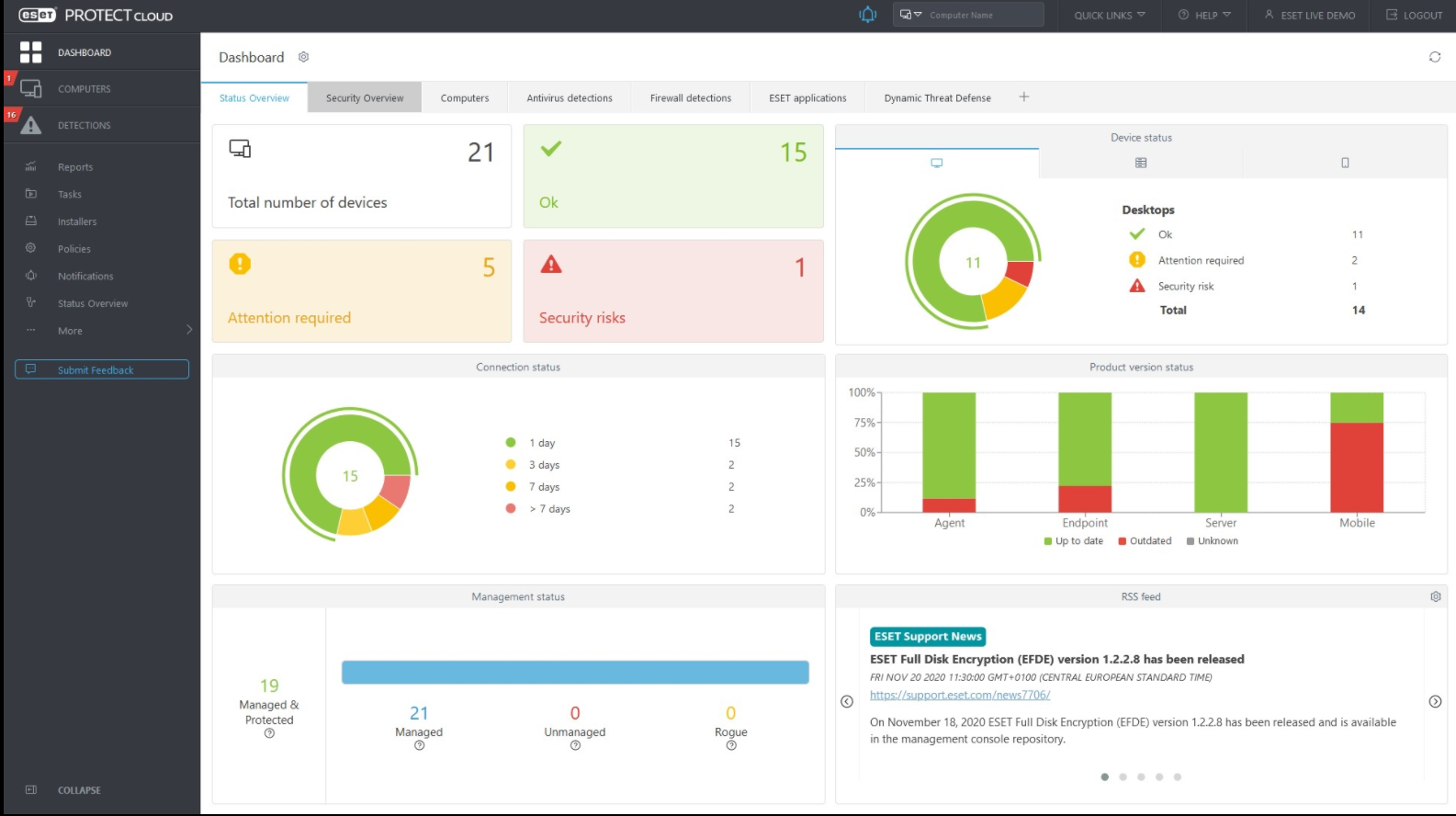
Increase the security of your endpoints and desktops with a proven and approved solution. ITrust Managed EDR provides a unified 360° view of your IT environment, rapid threat detection and remediation in real time!
Why ITrust Managed EDR ?
Why ITrust Managed EDR ?
- Deployment time: 1/2 day
- 24/7 monitoring
- Security threats detection
- Automated or manual remediation according to your preferences
- Quick intervention
- Respect for the sovereignty of your data (European solution not subject to the Patriot Act or the Cloud Act)
- State-approved and ISO 9001 certified.
Key data about the security of your devices
The average cost of a successful endpoint attack!
of successful attacks have targeted terminals!

ITrust Managed EDR for quick response and advice from cybersecurity experts
ITrust has been conducting MSSP activities since 2014, on proprietary and partner technologies. The service division guarantees you a high-performance and continuous 24-hour monitoring. Threats targeting your terminals are detected in a few minutes and immediately dealt with, either by an analyst’s intervention or via an automated remediation action. The monitoring procedures implemented, which are precise and continuously improved, are specific to ITrust and ISO9001 certified.
Our approach to secure your endpoints
Supervise
Daily monitoring and management of your endpoints by our expert cybersecurity analyst team, 24/7
Detect
Quick threats detection and client alerts using a certified methodology.
Remedy
Isolate the potentially infected workstation or server. Alert qualification by an analyst who will be able to identify a proven threat and treat it.
Advisory
A concret action plan is provided to ensure the continuity of yout business and the eradication of the threat.
Contact us
An initial discussion with our team will allow us to fully understand your objectives and provide you with a customized offer.