Reveelium
Reveelium is a behavioral analysis engine for detecting weak signals and anomalies in information systems. Reveelium has been developed to provide an expert anomaly detection system based on intelligent algorithms that ITrust has been developing for 5 years with the support of 3 international laboratories.
Weak signal analysis / Logical correlator / Shared knowledge base
ITrust expert in big data and cybersecurity
ITrust teams have been working since 2009 on intelligent systems capable of detecting weak signals within information systems to prevent unknown attacks and viruses. The experience of our engineers, acquired during forensic missions, audits or expert appraisals, has enabled us to model a behavioural engine to fight against APTs in particular.
Our team specializes in the decisional processing of security information from different applications, servers or security equipment.
Reveelium has been developed to provide an expert system of anomaly detection based on intelligent algorithms that ITrust has been developing for 5 years with the support of three international laboratories.
Within ITrust, we use big data and machine learning technologies to address cybersecurity issues.
You are looking for:
- Detect APT (Advanced Persistent Threat), Viruses and unknown attacks
- Detecting deviant behaviour within your information system
- Identifying weak signals as a precursor to a disaster
- Identify the loss and retrieval of confidential data
- Preventing the saturation of computer resources
General fonctions

3 out of 4 companies are subject to computer attacks or hacking (Verizon). 90% are nevertheless equipped with essential security equipment.
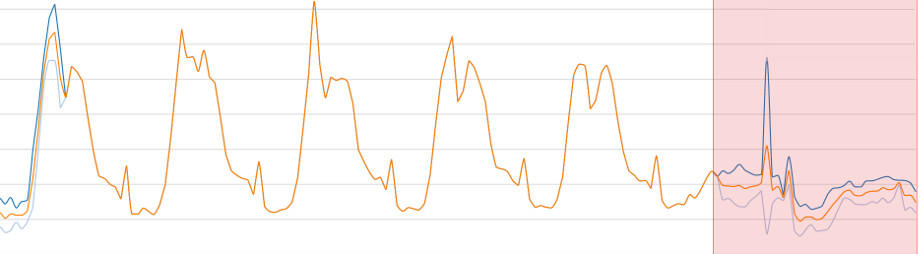
APTs (persistent threats), malicious behaviour or viruses go beyond existing security defences, and no current tool can detect these attacks.
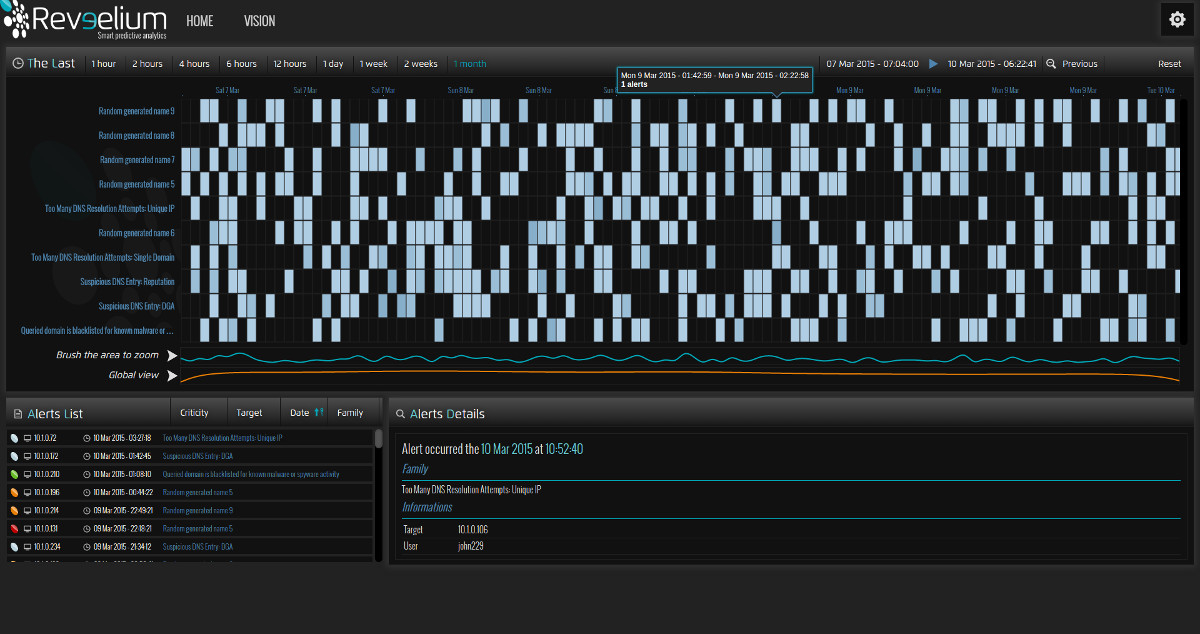
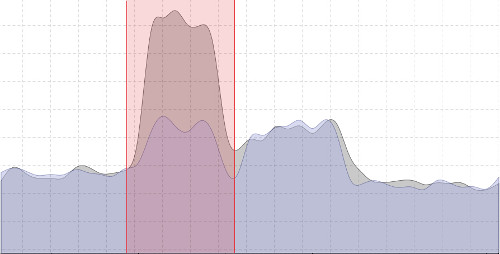
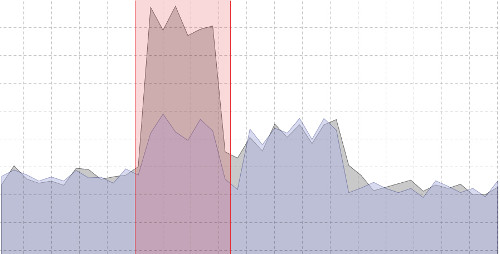
Yet they leave footprints in their path. Finding these malicious traces on a large amount of data and exploiting these signals is impossible with today’s tools.
It’s like looking for a needle in a haystack.
That’s what Reveelium can do !
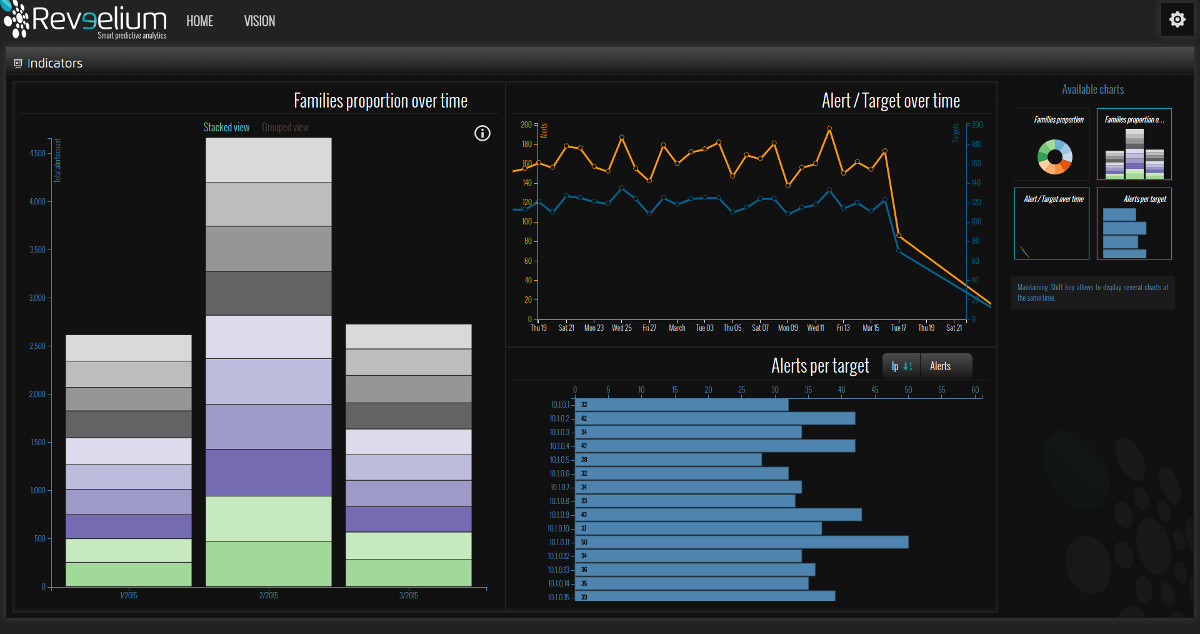
Reveelium finds these traces with its automated anomaly detection system.
Reveelium’s strong points
Production
Detects upstream of the impact and automates the analysis.
Security
- Significantly reduces the time it takes to search for traces of an incident
- Detects unknown, unforeseen events and incidents before they occur.
- Allows you to react and share instantaneously on an incident
- Detects the exploitation of an 0-Day by its abnormal character.
- Enables instant threat analysis rather than post-incident processing
Compliance and regulation
- Automates compliance (PCI, SoX, Bale3, HIPAA, HDS, EPrivacy)
- Allows compliance with recommendations for continuous monitoring (NIST, ANSSI)
- Allows incident management (NIST, ANSSI)
Use cases
Different use cases are detected by Reveelium :
- Forensics and investigation (e.g. identification and path of an attack)
- Avoid fraudulent use of the IS (e.g. detection of employee browsing on a prohibited website)
- Detecting rights theft
- Avoid loss of data, avoid espionage (e.g. detection of data export in large quantities on a dangerous PIN).
- Detect viruses and unknown attacks and APTs
- Predict a crash, a production unavailability (e.g. predict resource saturation)
- Remaining compliant with regulations or best practices
- Avoid financial loss
- Avoiding a legal risk
- Detecting a brand image attack
- Maintains in operational conditions (MCO)
For details of these use cases, contact us.
Features and Characteristic
Reveelium is a new generation safety tool whose richness and strength lies in the use of 3 complementary engines.
1/ Weak signal detection engine – resulting from advanced research in mathematical algorithms.
2/ Business correlation engine that complements the previous one – resulting from the experience of safety engineers and consultants.
3/ Global knowledge base on which the two engines are based – this is Reveelium’s memory, which identifies and collects the behaviour of all Reveelium customers, so that each of them can benefit from the experience of the others.
All these 3 engines work on an outsourced big data base capable of processing large quantities of data.
Business rules can be implemented and followed in the business correlator. The GUI can display correlations and track deviations, allowing user interaction and feedback. The Reveelium technology is unique in the world.
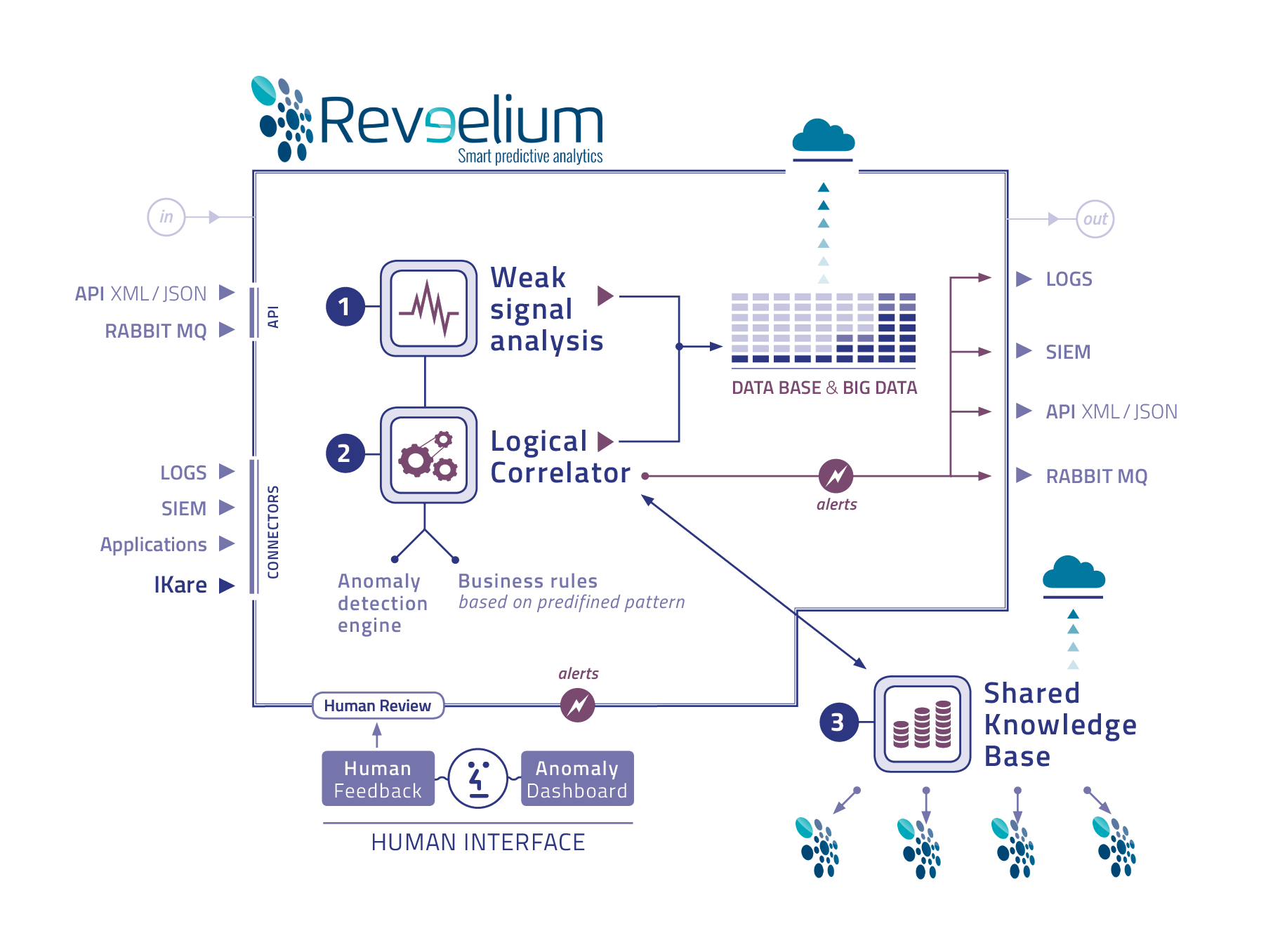
1/ Analysis & Learning
- Analytical statistics
- Learning process
- Data Source Profile
2/ Correlation et Intelligence
- Correlation of the analysis of the different sources
- System Power Expert
- Deviation of the data sample
3/ Shared knowledge base
Reveelium is able to process different input data
- Data from SIEM sources and Logs (SIEM connector)
- AMQP messages (Rabit MQ,…)
- Reveelium API queries (JSON)
Reveelium returns alerts and anomaly thresholds (and their source) by :
- Logs (SIEM connectors)
- Syslogs
- AMQP
- XML/JSON
Our value proposition compared to other tools
- Immediate ROI: the new generation 3D technology (weak signal, business correlation, KB) is unique in the world, allowing a 20-fold reduction in false positives and a detection time that goes from 12 months on average to 1 week.
- Reveelium’s detection capacity increases the productivity and the analysis capacity of the teams in charge of supervision. The tool allows to divide by 50 the time of data analysis by the supervisors (example: the processing time of a forensic incident which took 50 hours at the University of Toulouse was achieved in 1 hour by Reveelium).
- 3D technology allows to detect anomalies (viruses, behaviors, frauds, leaks, malevolence) where no other tool is able to do so.
- Reveelium and its universal connector allows to process all types of data from all possible sources
- Reveelium is easy to install: very simple installation in SaaS on premise, backed by a private cloud. Does not require complex installation of other modules. The technology can be based on any existing tool (SIEM, AD, application, etc …). The installation has no impact on the operation of the IS. (example: ITT as a plugin on the SIEM Kibana/Logstash, can be installed in 1h and requires little customization. There is no impact on the IS and existing applications).
- The interface and the use in learning mode allow a very simple installation and use for the decision-makers.
- Reveelium can be completed by a SIEM module for customers who do not have data centralization.
- The technology is not subject to the Patriot Act – customer data remains confidential.
Delivery and modules
Reveelium is offered in SaaS on Premise or external as a virtual machine.
Reveelium Log Engine is proposed as a plugin for SIEM (through a SIEM connector)
or
Reveelium SOC including all the supervision platform: logging, correlation logs, and alerts by Reveelium
or
Reveelium Forensique – offered as a SaaS application in which customers can send their logs for forensic processing in search of abnormalities.
or
As a plugin on business applications, looking for business anomalies (AD, Messaging, etc…)
The best way to discover and exploit the unique capabilities offered by Reveelium is to build a mock-up on full-scale production data, involving our consultants.